Hey folks,
Is it possible to share the routes from the Wireguard containers with other containers?
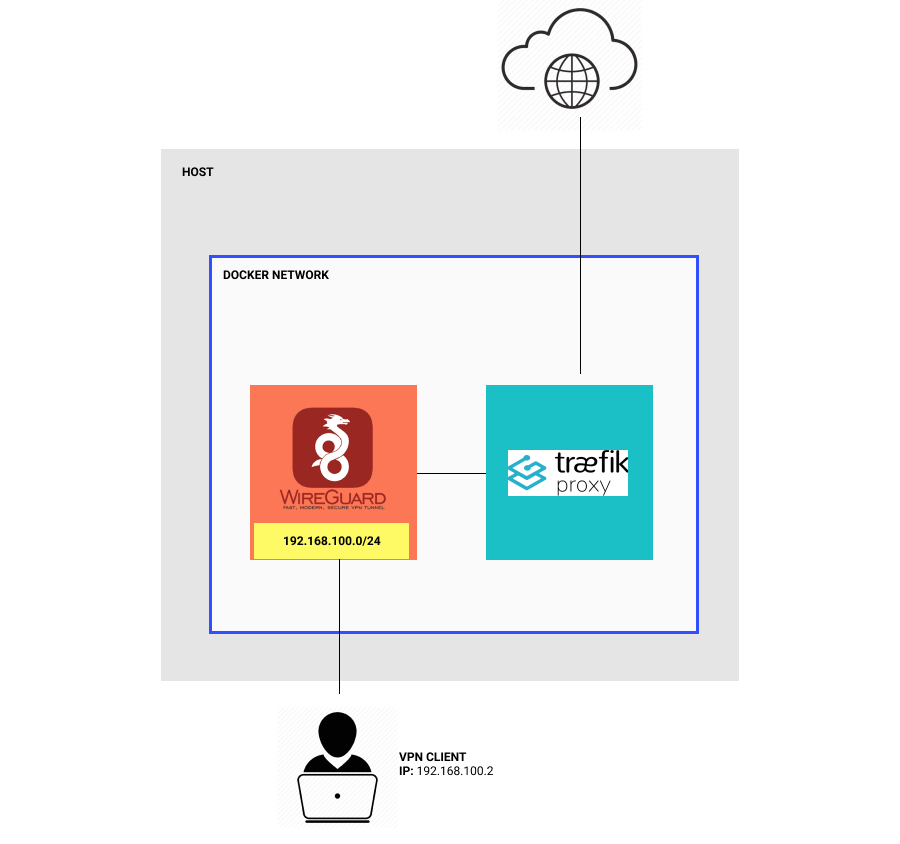
What I’m trying to do
- I’d like people to connect into my Wireguard server running on a docker container shared with Traefik (they would have a 192.168.100.0/24 address)
- Traefik would be able to route web requests to web servers running on the VPN client’s local machine
My problem
- I cannot get the Traefik container to ping
192.168.100.2
My workaround
- If I install Wireguard directly on the host (without using the container), Traefik is able to see the
192.168.100.2 client
My question
Is it possible for Traefik to be able to ping the VPN client when Wireguard is running in its own container?
More details
My host:
- Ubuntu 20.04
- Docker version 20.10.6, build 370c289
Here is a picture visualizing what I am trying to do.
Thank you for your help! 
Here is my docker-compose.yml file if anyone has any thoughts:
version: '3.7'
services:
traefik:
image: traefik:v2.4
restart: always
networks:
- web-public
ports:
# Listen on port 80, default for HTTP, necessary to redirect to HTTPS
- target: 80
published: 80
mode: host
# Listen on port 443, default for HTTPS
- target: 443
published: 443
mode: host
volumes:
# Add Docker as a mounted volume, so that Traefik can read the labels of other services
- /var/run/docker.sock:/var/run/docker.sock:ro
- ./traefik.yml:/traefik.yml:ro
- ./traefik-tunnel-dynamic-conf.yml:/traefik-tunnel-dynamic-conf.yml
- ./certificates/acme.json:/certificates/acme.json
wireguard:
image: ghcr.io/linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=UTC
- SERVERURL=myserver.mydomain.test
- SERVERPORT=51820
- PEERS=my-peer
- PEERDNS=1.1.1.1,1.0.0.1
- INTERNAL_SUBNET=192.168.100.0
- ALLOWEDIPS=0.0.0.0/0
volumes:
- config:/config
- /lib/modules:/lib/modules
ports:
- "51820:51820/udp"
networks:
- web-public
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped
volumes:
config:
networks:
web-public:
external: true
With this config
- I can connect a client to the VPN (getting a 192.168.100.X address)
- That client can get to the Internet
- The Traefik container cannot ping the client at 192.168.100.X
Let me know if you have any other questions!
wireguard nats that vpn
so it’s something like 192.168.100.2 → natted to 172.16.0.5 (pretend this is the ip of the wg container) so traefik has no clue about that natted network. You would need to build routes in traefik to go directly like that.
if communications SOURCE from the client, it should work fine (mine does) because that traffic gets natted, return traffic hits your docker host and is natted based on the port (PAT) used back to the appropriate container which then nats it to the vpn subnet. in your case above, they’re both on the same docker network, so we can ignore the host layer of the nat, but traefik still has no clue that there is a 192.168.100.0/24 network. You could probably add it in with something like ip route add 192.168.100.0/24 via <wireguard container ip> dev eth0 but im making a bit of a guess here… im also not sure why pinging from traefik to wg clients matters since they should be able to leverage traefik as a proxy regardless…

![]()