Hi,
I have sveral containers running on my VPS. Last night, I installed Linuxserver/wireguard on the same VPS. It works fine and it’s so fast that I couldn’t tell if the VPN is on or off.
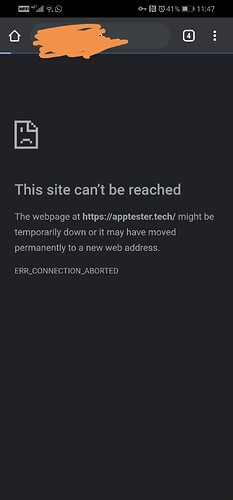
However, I have a problem that when I start VPN either on my phone, which is Android or windows laptop, I cannot access my personal domain that is pointing to the other containers on the same VPS. It shows that the site cann’t be reached as follow:
I am pretty sure that it is DNS problem because I tried to run the container on network_mode: host and the log showed that port 53 is already in use, and I think the solution would do with iptables staff, which I don’t fully understand.
Anyone has faced the same problem?
what did you set as the dns in your docker compose?
Here is my settings:
version: "2.1"
services:
wireguard:
image: linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=Europe/London
# - SERVERURL=wireguard.domain.com #optional
- SERVERPORT=51820 #optional
- PEERS=1 #optional
- PEERDNS=8.8.8.8, 8.8.4.4 #optional
- INTERNAL_SUBNET=10.13.13.0 #optional
volumes:
- ./config:/config
- /lib/modules:/lib/modules
ports:
- 51820:51820/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped
I also tried to add dns option in the docker-compose as follow
dns:
- 8.8.8.8
- 8.8.4.4
but that doesn’t work as well. Then, I thought to my self that all my other containers are runing behind reverse proxy Traefik.
So, I also change the above settings to the following:
version: "2.1"
services:
wireguard:
image: linuxserver/wireguard
container_name: wireguard
cap_add:
- NET_ADMIN
- SYS_MODULE
environment:
- PUID=1000
- PGID=1000
- TZ=Europe/London
# - SERVERURL=wireguard #optional
# - SERVERPORT=51820 #optional
- PEERS=1 #optional
- PEERDNS=8.8.8.8,8.8.4.4 #optional
# - INTERNAL_SUBNET=10.13.13.0 #optional
volumes:
- ./config:/config
- /lib/modules:/lib/modules
# ports:
# - 51820:51820/udp
sysctls:
- net.ipv4.conf.all.src_valid_mark=1
restart: unless-stopped
labels:
- traefik.enable=true
- traefik.docker.network=traefik-web
- traefik.udp.routers.udp.entrypoints=udps
- traefik.udp.services.udp.loadbalancer.server.port=51820
dns:
- 8.8.8.8
- 8.8.4.4
The above works fine and I can browse other websites but I still cannot access my own domain.
when you are on your LAN (not vpn) can you resolve the domains? are you using internal dns to do this or hairpinning the connection?
my bad, i forgot we’re on a vps here. so outside of the vpn, if you goto .yourdomain.com it goes to the stuff hosted on the vps and works fine, when you vpn into the vps, it fails? I believe this is a hairpinning issue (quite common for a public facing provider to block this).
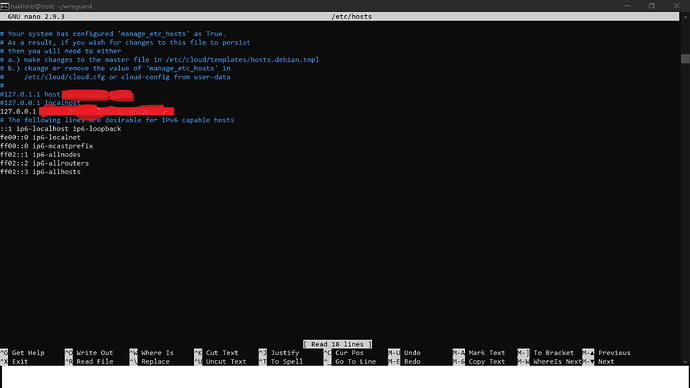
do you have root access on the vps? if yes, try creating a hosts entry for one of the things you can’t reach, using the internal ip address (or perhaps even 127.0.0.1) and see what happens
yes, I have root access to the vps and I edited the hosts file but still no access when vpn is on.
I just want to mention I also tested linexserver/openvpn-as, it works fine and I can access my own domain but I prefer Wireguard.
I ran wireguard on the host network_mode: host and I can access my own domain. but there is a problem that the log says that port 53 is already in use.
As far as I am concerned that I could access to my own domain when runing on host network because the dns of container couldn’t run and it used the host dns instead.
So the solution would be forwarding the container’s dns port (53) to the host’s port (53), therfore the host dns takes full control.
Can anyone please help me with? forwarding the container’s dns to host’s container
Run it with bridge networking and built in coredns forwards to host’s dns by default. You need to set the dns var to auto to utilize that.
It’s in the readme
If you would be so kind, could you explain in detail?
I think l left out a few details:
I already have 5 containers running:
Container 1 point to traefik.&&.com (subdomain)
Container 2 point to cloud.&&.com (subdomain)
Container 3 point to api.&&.com (subdomain)
Container 4 point to &&.com (main domain)
Container 5 point to oauth.&&.com (subdomain)
The sixth container will be vpn.&&. com (subdomain)
Without VPN wireguard running on my phone, I can browse these domains and they are accessible from anywhere, but once i start running VPN wireguard on my phone, these domains are not accessible.but I can access them on other device that is not running my wireguard vpn.
All of these containers are running on a VPS.
I hope I make it clear.
I found out that ufw was blocking the connection so I had to look ufw’s log and see what interface is being blocked and I just allowed the interface for in and out to anyport and that fixed the problem.
Thanks for coming back to let us know and glad to hear you figured it out. I was out of ideas. But I should have known because ufw seems to be at the center of most if not all networking issues we get asked about.